IDA伪代码:
id __cdecl +[IMNetworkManager sharedInstance](IMNetworkManager_meta *self, SEL a2)
{
unsigned __int64 v2; // x10
int *v3; // x8
int v4; // t1
signed int v5; // w9
__int64 v6; // x13
signed int v7; // w12
unsigned __int64 v8; // x11
unsigned int v9; // w10
int *v10; // x11
int v11; // t1
id result; // x0
__int64 v13; // x0
unsigned __int8 *v14; // x19
char *v15; // x20
char *v16; // x20
__int64 v17; // x11
signed __int64 v18; // x21
__int64 v19; // x10
pthread_t v20; // x0
bool v21; // zf
bool v22; // zf
signed int v23; // w8
int v24; // w9
__int64 v25; // x8
unsigned __int64 v26; // x9
unsigned int v27; // w8
_QWORD *v28; // x12
Dl_info v29; // [xsp+8h] [xbp-98h]
char v30[8]; // [xsp+28h] [xbp-78h]
__int64 v31; // [xsp+30h] [xbp-70h]
char v32[14]; // [xsp+38h] [xbp-68h]
__int64 v33; // [xsp+48h] [xbp-58h]
__int64 vars0; // [xsp+A0h] [xbp+0h]
// 前几次跳过
//
if ( (unsigned __int64)++qword_103F04118 < 0x15 )// 前几次跳过
{
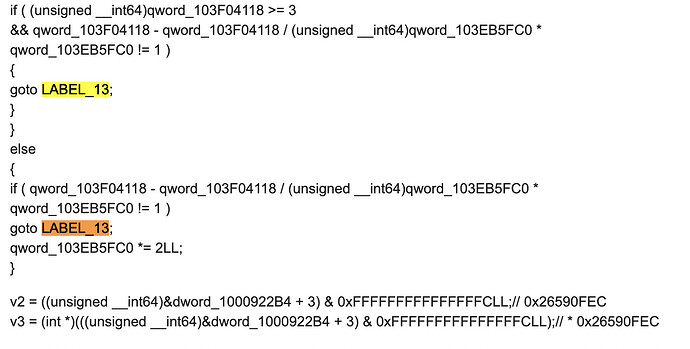
if ( (unsigned __int64)qword_103F04118 >= 3
&& qword_103F04118 - qword_103F04118 / (unsigned __int64)qword_103EB5FC0 * qword_103EB5FC0 != 1 )
{
goto LABEL_13;
}
}
else
{
if ( qword_103F04118 - qword_103F04118 / (unsigned __int64)qword_103EB5FC0 * qword_103EB5FC0 != 1 )
goto LABEL_13;
qword_103EB5FC0 *= 2LL;
}
v2 = ((unsigned __int64)&dword_1000922B4 + 3) & 0xFFFFFFFFFFFFFFFCLL;// 0x26590FEC
v3 = (int *)(((unsigned __int64)&dword_1000922B4 + 3) & 0xFFFFFFFFFFFFFFFCLL);// * 0x26590FEC
do
{
v4 = *v3;
++v3;
v2 += 4LL;
}
while ( v4 != 643370988 );
v5 = -1820720928;
v6 = v3[1];
v7 = (*v3 ^ 0xB7568CAD) + (v6 ^ 0xF91807F6) + 1;
if ( v7 >= 4 )
{
v8 = (v6 ^ 0xFFFFFFFFF91807F6LL) + v2;
v9 = ((unsigned int)v7 >> 2) + 1;
v10 = (int *)(v8 - 4);
do
{
v11 = *v10;
–v10;
v5 ^= v11;
–v9;
}
while ( v9 > 1 );
}
if ( v5 != (v3[2] ^ 0xAF219B75) )
JUMPOUT(0xB5A96000uLL);
LABEL_13:
sub_1000926CC();
result = (id)objc_getClass(“IMNetworkManager”);
if ( (unsigned __int64)++qword_103F04260 < 0x15 )
{
if ( (unsigned __int64)qword_103F04260 >= 3
&& qword_103F04260 - qword_103F04260 / (unsigned __int64)qword_103EB6010 * qword_103EB6010 != 1 )
{
goto LABEL_54;
}
}
else
{
if ( qword_103F04260 - qword_103F04260 / (unsigned __int64)qword_103EB6010 * qword_103EB6010 != 1 )
goto LABEL_54;
qword_103EB6010 *= 2LL;
}
v13 = class_getClassMethod(result, “sharedInstance”);
result = (id)method_getImplementation(v13);
if ( !result )
goto LABEL_54;
v14 = (unsigned __int8 *)result;
result = (id)dladdr(result, &v29);
if ( !(_DWORD)result )
goto LABEL_54;
v15 = v29.var0;
result = (id)strstr(v29.var0, “/System/Library/PrivateFrameworks/”);
if ( result )
goto LABEL_54;
result = (id)strstr(v15, “/System/Library/Frameworks/”);
if ( result )
goto LABEL_54;
result = (id)strstr(v15, “/usr/lib/”);
if ( result )
goto LABEL_54;
v16 = strstr(v15, “/Library/MobileSubstrate/DynamicLibraries/”);
if ( byte_103EB6018[0] & 1 )
{
v17 = 0LL;
do
{
byte_103F04268[v17] = (v17 + 100) ^ byte_103EB6018[v17 + 1];
++v17;
}
while ( v17 != 23 );
byte_103EB6018[0] = 52;
}
v18 = mac_syscall(SYS_access, byte_103F04268, 0);
if ( byte_103EB6030[0] & 1 )
{
v19 = 0LL;
do
{
byte_103F0427F[v19] = (v19 - 69) ^ byte_103EB6030[v19 + 1];
++v19;
}
while ( v19 != 12 );
byte_103EB6030[0] = -84;
}
*(_QWORD *)v30 = 0LL;
v31 = 0LL;
*(_QWORD *)&v32[6] = 0LL;
*(_QWORD )v32 = 0LL;
v20 = pthread_self();
pthread_getname_np(v20, v30, 29LL);
result = (id)strstr(v30, byte_103F0427F);
if ( result )
v21 = 0;
else
v21 = v18 == 2;
if ( v21 )
v22 = v16 == 0LL;
else
v22 = 0;
v23 = !v22;
v24 = v14[3];
if ( (v24 & 0xFC) != 20 )
{
if ( (v24 & 0xFFFFFF9F) != 144 && (v24 & 0xFFFFFFFB) != 88 || v14[4] & 0x1F || v14[5] > 3u || v14[6] != 31 )
{
if ( !v23 )
goto LABEL_54;
}
else if ( v14[7] != 214 && (v23 ^ 1) & 1 )
{
goto LABEL_54;
}
}
v25 = 0LL;
v26 = 667486422LL;
do
{
v26 += ((__int64 *)((char *)&vars0 + v25) ^ 0xFFFFFFFF809CD1FELL) + 1;
*(__int64 *)((char *)&vars0 + v25) = v26 >> 9;
v25 += 8LL;
}
while ( v25 != 336 );
if ( v26 )
JUMPOUT(0xB5A98000uLL);
LABEL_54:
LODWORD(v29.var0) = 311;
v27 = 4;
v28 = &unk_103F04000;
while ( 1 )
{
switch ( v27 )
{
case 0u:
goto LABEL_62;
case 1u:
if ( v28[34] != -1LL )
{
result = (id)dispatch_once(&qword_103F04110, &off_103755998);
v28 = (_QWORD *)&unk_103F04000;
}
LODWORD(v29.var0) = 306;
v27 = 8;
continue;
case 4u:
*(_DWORD *)v30 = LODWORD(v29.var0) - 43 * ((unsigned int)(51935 * LODWORD(v29.var0)) >> 21);
v27 = 11 - (LODWORD(v29.var0) - 43 * ((unsigned int)(51935 * LODWORD(v29.var0)) >> 21));
LODWORD(v29.var0) = 310 - (LODWORD(v29.var0) - 43 * ((unsigned int)(51935 * LODWORD(v29.var0)) >> 21));
break;
case 6u:
result = (id)objc_retain(qword_103F04108);
LABEL_62:
if ( __stack_chk_guard == v33 )
result = (id)objc_autoreleaseReturnValue(result);
return result;
case 8u:
*(_DWORD *)v30 = LODWORD(v29.var0) - 93 * ((unsigned int)(52106 * LODWORD(v29.var0)) >> 22);
v27 = 33 - (LODWORD(v29.var0) - 93 * ((unsigned int)(52106 * LODWORD(v29.var0)) >> 22));
LODWORD(v29.var0) = 332 - (LODWORD(v29.var0) - 93 * ((unsigned int)(52106 * LODWORD(v29.var0)) >> 22));
break;
default:
continue;
}
}
}