前期砸壳、class-dump等过程不表,直接切入正题。
先简单描述一下注册流程,需要用户输入邮箱和密码,然后客户端向服务器发起HTTPS请求
例如:
邮箱:ggthg@163.com
密码:xx123456
https://api.passport.pptv.com/v3/register/nonveri_email_simple.do?format=json&infovalue=lUgLoJfAgz9Yfc321gZzjb%2Fnkj800Neq8KuaPJYThV4%3D&index=02
其中三个参数,format=json不用说了,最后的index=02是固定值也不用说了,重点就是infovalue , 它是邮用户输入的邮箱和密码经过URL转义,然后调用[PPEncryptOrDecryptClass doCipher:operation:index:]生成的,上家伙(LLDB+IDA)
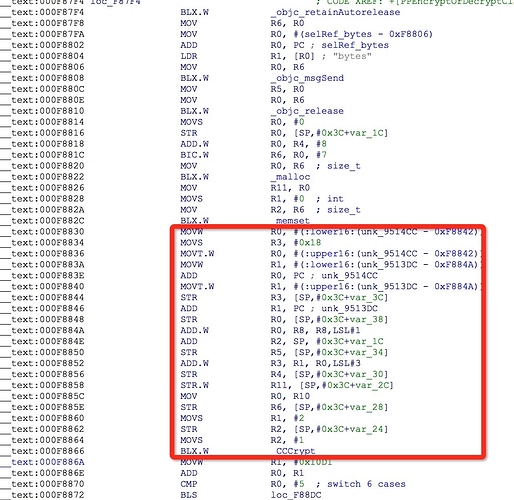
经过多次运行,发现生成结果不随时间变化,然后我偷偷F5了一下,重点是中间那个长函数体,代码如下
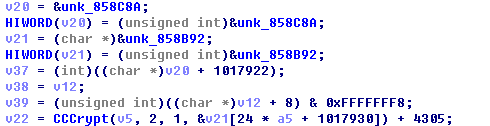
这里执行了一个CCCrypt的函数,通过我在GitHub上找到的一份老代码判断,它应该是长这个样子:
ccStatus = CCCrypt(arg2,
kCCAlgorithm3DES,
kCCOptionPKCS7Padding,
vkey[0],
kCCKeySize3DES,
vinitVec[arg3],
vplainText,
plainTextBufferSize,
(void*)bufferPtr,
bufferPtrSize,
&movedBytes);
我需要知道的是vkey[?]和[vinitVec[?]这个在最新的代码中具体是什么,从汇编代码里面看到
__text:000F8830 MOVW R0, #(:lower16:(unk_9514CC - 0xF8842))
__text:000F8834 MOVS R3, #0x18
__text:000F8836 MOVT.W R0, #(:upper16:(unk_9514CC - 0xF8842))
__text:000F883A MOVW R1, #(:lower16:(unk_9513DC - 0xF884A))
__text:000F883E ADD R0, PC ; unk_9514CC
__text:000F8840 MOVT.W R1, #(:upper16:(unk_9513DC - 0xF884A))
__text:000F8844 STR R3, [SP,#0x3C+var_3C]
__text:000F8846 ADD R1, PC ; unk_9513DC
__text:000F8848 STR R0, [SP,#0x3C+var_38]
__text:000F884A ADD.W **R0, R8, R8,LSL#1**
__text:000F884E ADD R2, SP, #0x3C+var_1C
__text:000F8850 STR R5, [SP,#0x3C+var_34]
__text:000F8852 ADD.W **R3, R1, R0,LSL#3**
lower16和upper16应该怎么理解?LSL#1好像有左移操作在里面,另外,unk_9514CC和unk_9513DC就代码未处理的字符串吧,那好像是个数组,通过传值来取具体的字符串出来,比如:
Byte vkey[][24] = {
{0x15,0xB9,0xFD,0xAE,0xDA,0x40,0xF8,0x6B,0xF7,0x1C,0x73,0x29,0x25,0x16,0x92,0x4A,0x29,0x4F,0xC8,0xBA,0x31,0xB6,0xE9,0xEA},
{0x15,0xB9,0xFD,0xAE,0xDA,0x40,0xF8,0x6B,0xF7,0x1C,0x73,0x29,0x25,0x16,0x92,0x4A,0x29,0x4F,0xC8,0xBA,0x31,0xB6,0xE9,0xEA},
{0x29,0x02,0x8A,0x76,0x98,0xEF,0x4C,0x6D,0x3D,0x25,0x2F,0x02,0xF4,0xF7,0x9D,0x58,0x15,0x38,0x9D,0xF1,0x85,0x25,0xD3,0x26},
{0xD0,0x46,0xE6,0xB6,0xA4,0xA8,0x5E,0xB6,0xC4,0x4C,0x73,0x37,0x2A,0x0D,0x5D,0xF1,0xAE,0x76,0x40,0x51,0x73,0xB3,0xD5,0xEC},
{0x43,0x52,0x29,0xC8,0xF7,0x98,0x31,0x13,0x19,0x23,0xF1,0x8C,0x5D,0xE3,0x2F,0x25,0x3E,0x2A,0xF2,0xAD,0x34,0x8C,0x46,0x15},
{0x9B,0x29,0x15,0xA7,0x2F,0x83,0x29,0xA2,0xFE,0x6B,0x68,0x1C,0x8A,0xAE,0x1F,0x97,0xAB,0xA8,0xD9,0xD5,0x85,0x76,0xAB,0x20},
{0xB3,0xB0,0xCD,0x83,0x0D,0x92,0xCB,0x37,0x20,0xA1,0x3E,0xF4,0xD9,0x3B,0x1A,0x13,0x3D,0xA4,0x49,0x76,0x67,0xF7,0x51,0x91},
{0xAD,0x32,0x7A,0xFB,0x5E,0x19,0xD0,0x23,0x15,0x0E,0x38,0x2F,0x6D,0x3B,0x3E,0xB5,0xB6,0x31,0x91,0x20,0x64,0x9D,0x31,0xF8},
{0xC4,0x2F,0x31,0xB0,0x08,0xBF,0x25,0x70,0x67,0xAB,0xF1,0x15,0xE0,0x34,0x6E,0x29,0x23,0x13,0xC7,0x46,0xB3,0x58,0x1F,0xB0},
{0x52,0x9B,0x75,0xBA,0xE0,0xCE,0x20,0x38,0x46,0x67,0x04,0xA8,0x6D,0x98,0x5E,0x1C,0x25,0x57,0x23,0x0D,0xDF,0x31,0x1A,0xBC},
{0x8A,0x52,0x9D,0x5D,0xCE,0x91,0xFE,0xE3,0x9E,0x9E,0xE9,0x54,0x5D,0xF4,0x2C,0x3D,0x9D,0xEC,0x2F,0x76,0x7C,0x89,0xCE,0xAB}
};
但我自己用老版本的代码生成了一个app放在IDA中,却显示的和它的不一样,情况就是这样,希望有经验的朋友们一起帮忙看看,谢谢。