一、前言
由于我最多就只会去去广告这样子,在打算搞去广告的时候发现了debugserver启动应用失败
iPhone:~ root# debugserver -x auto 127.0.0.1:2345 /var/containers/Bundle/Application/C8B07D97-46C7-4CFD-BD06-FD03A5F1667C/heixiazi.app/heixiazi
debugserver-@(#)PROGRAM:debugserver PROJECT:debugserver-360.0.26.1
for arm64.
Segmentation fault: 11
看起来这个应用是有做反调试的,和大佬的这个帖子的情况非常像
http://bbs.iosre.com/t/7-2-0-ios/770?u=wstclzy2010
参照这个帖子,才有了以下绕过反调试的办法。
二、动态调试
以backboard方式启动应用
iPhone:~ root# debugserver -x backboard *:2345 /var/containers/Bundle/Application/C8B07D97-46C7-4CFD-BD06-FD03A5F1667C/heixiazi.app/heixiazi
debugserver-@(#)PROGRAM:debugserver PROJECT:debugserver-360.0.26.1
for arm64.
Listening to port 2345 for a connection from *...
对ptrace下断点:
(lldb) b ptrace
Breakpoint 1: no locations (pending).
WARNING: Unable to resolve breakpoint to any actual locations.
(lldb) c
Process 5729 resuming
Process 5729 stopped
* thread #1, queue = 'com.apple.main-thread', stop reason = breakpoint 1.1
frame #0: 0x00000001914f5078 libsystem_kernel.dylib`__ptrace
libsystem_kernel.dylib`__ptrace:
-> 0x1914f5078 <+0>: adrp x9, 160475
0x1914f507c <+4>: add x9, x9, #0x2e8 ; =0x2e8
0x1914f5080 <+8>: str wzr, [x9]
0x1914f5084 <+12>: mov x16, #0x1a
0x1914f5088 <+16>: svc #0x80
0x1914f508c <+20>: b.lo 0x1914f50a4 ; <+44>
0x1914f5090 <+24>: stp x29, x30, [sp, #-0x10]!
0x1914f5094 <+28>: mov x29, sp
Target 0: (heixiazi) stopped.
拿到lr寄存器的地址:
`(lldb) im li -o -f | grep heixiazi
[ 0] 0x0000000000054000 /private/var/containers/Bundle/Application/C8B07D97-46C7-4CFD-BD06-FD03A5F1667C/heixiazi.app/heixiazi(0x0000000100054000)
(lldb) p/x $lr
(unsigned long) $4 = 0x000000010010e048
得到ida中的偏移为0x10010e048 - 0x54000 = 0x1000BA048
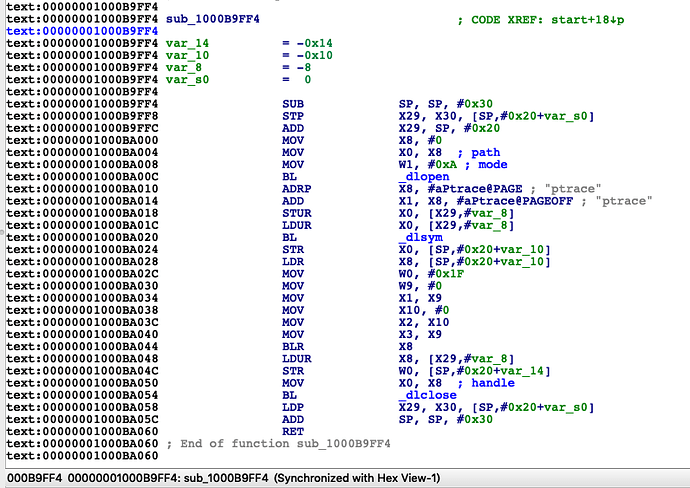
三、静态分析
在ida中G到1000BA048
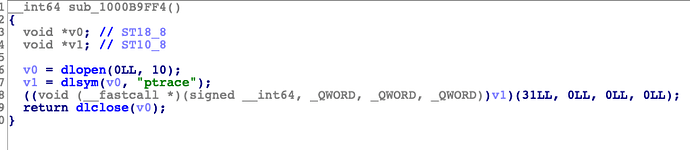
得到应用是在start中有个函数sub_1000B9FF4调用了ptrace实现反调试
两个方法
①简单点的、一次性的
在lldb中绕过反调试
给sub_1000B9FF4函数下断点:
(lldb) im li -o -f | heixiazi
[ 0] 0x00000000000a8000 /private/var/containers/Bundle/Application/C8B07D97-46C7-4CFD-BD06-FD03A5F1667C/heixiazi.app/heixiazi(0x00000001000a8000)
(lldb) br s -a '0xa8000+0x1000B9FF4'
Breakpoint 1: where = heixiazi`___lldb_unnamed_symbol2426$$heixiazi, address = 0x0000000100161ff4
(lldb) c
Process 5738 resuming
Process 5738 stopped
* thread #1, queue = 'com.apple.main-thread', stop reason = breakpoint 1.1
frame #0: 0x0000000100161ff4 heixiazi`___lldb_unnamed_symbol2426$$heixiazi
heixiazi`___lldb_unnamed_symbol2426$$heixiazi:
-> 0x100161ff4 <+0>: sub sp, sp, #0x30 ; =0x30
0x100161ff8 <+4>: stp x29, x30, [sp, #0x20]
0x100161ffc <+8>: add x29, sp, #0x20 ; =0x20
0x100162000 <+12>: mov x8, #0x0
0x100162004 <+16>: mov x0, x8
0x100162008 <+20>: mov w1, #0xa
0x10016200c <+24>: bl 0x1021aca90 ; symbol stub for: dlopen
0x100162010 <+28>: adrp x8, 8279
Target 0: (heixiazi) stopped.
直接在遇到sub_1000B9FF4函数时return掉:
(lldb) thread return
* thread #1, queue = 'com.apple.main-thread', stop reason = breakpoint 1.1
frame #0: 0x0000000100162080 heixiazi`___lldb_unnamed_symbol2427$$heixiazi + 28
heixiazi`___lldb_unnamed_symbol2427$$heixiazi:
-> 0x100162080 <+28>: bl 0x1021ad3cc ; symbol stub for: objc_autoreleasePoolPush
0x100162084 <+32>: adrp x8, 11534
0x100162088 <+36>: add x8, x8, #0xbe0 ; =0xbe0
0x10016208c <+40>: adrp x9, 11586
0x100162090 <+44>: add x9, x9, #0x4d0 ; =0x4d0
0x100162094 <+48>: ldur w10, [x29, #-0x8]
0x100162098 <+52>: ldur x1, [x29, #-0x10]
0x10016209c <+56>: ldr x9, [x9]
(lldb) c
Process 5738 resuming
2020-06-27 12:40:48.814 heixiazi[5738:259986] Safe mode check passed.
2020-06-27 12:40:49.055 heixiazi[5738:259986] TY_Info*****去VPN检测权限关闭
2020-06-27 12:40:49.055 heixiazi[5738:259986] TY_Info*****非去广告-代理检测
2020-06-27 12:40:49.064 heixiazi[5738:259986] TY_Info*****设备已越狱
2:40:49.064 heixiazi[5738:259986] TY_Info*****check明细——————(null)
可以看到成功进入应用了
②复杂一点、一劳永逸的
编写插件:
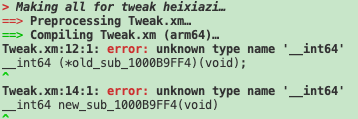
(要注意的是tweak.x是不行的,必须tweak.xm)
注意返回值类型为__int64,报错(其实就是int)
还有因为是arm64的设备要注意去掉后面的” | 0x1“:
#import <substrate.h>
#import <mach-o/dyld.h>
#import <dlfcn.h>
int (*old_sub_1000B9FF4)(void);
int new_sub_1000B9FF4(void)
{
NSLog(@"反反调试成功~~~~~~~~~");
return 0;
}
%ctor
{
@autoreleasepool
{
unsigned long _sub_1000B9FF4 = (_dyld_get_image_vmaddr_slide(0) + 0x1000B9FF4);
if (_sub_1000B9FF4) NSLog(@"发现 sub_1000B9FF4!");
MSHookFunction((void *)_sub_1000B9FF4, (void *)&new_sub_1000B9FF4, (void **)&old_sub_1000B9FF4);
}
}
这样就能正常debugserver启动应用了
iPhone:~ root# debugserver -x auto 127.0.0.1:2345 /var/containers/Bundle/Application/C8B07D97-46C7-4CFD-BD06-FD03A5F1667C/heixiazi.app/heixiazi
debugserver-@(#)PROGRAM:debugserver PROJECT:debugserver-360.0.26.1
for arm64.
Listening to port 2345 for a connection from 127.0.0.1...
(lldb) c
Process 6489 resuming
2020-06-27 13:31:16.765 heixiazi[6489:275139] LookinServer - Will launch. Framework version: 1.0.0
2020-06-27 13:31:16.766 heixiazi[6489:275139] [+] LookinLoader loaded!
2020-06-27 13:31:16.847 heixiazi[6489:275139] 发现 sub_1000B9FF4!
2020-06-27 13:31:16.969 heixiazi[6489:275139] 反反调试成功~~~~~~~~~
2020-06-27 13:31:17.639 heixiazi[6489:275139] Safe mode check passed.
2020-06-27 13:31:17.750 heixiazi[6489:275139] LookinServer - Trying to connect ...