Hey guys,
I’m stuck on a problem since few days… I’m trying to reverse engineer the WhatsApp iOS API. I’ve found a way to understand how almost all parts of a query are generated but there is still one where I’m stuck on.
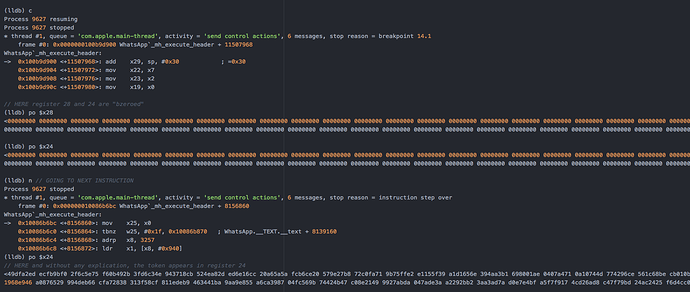
I’ve logified as much functions as possible, and figured out exactly where the token appear for the first time in assembly code.
As you can see on the following capture, at some point, registers x28 and x28 are “bytes zeroed” and on next step they are filled with the encrypted token bytes. I’m not able to see any function or sub procedur call. This encrypted value seems to born from anywhere.
I’ve tried to log all symetric and assymetric cryptography functions the app uses, they are not called on this operation.
I’ve also tried to manualy decrypt the token (or encrypt and compare assumed values), since I have at each runtime the private / private key and potential encrypted value, but I have no result.
My questions:
- Does someone could give me a methodology on how to proceed, or any other information ?
- The key used for decryption process is 256bit length. It seems to be too week for RSA. I’ve tested few assymetric / symetric methods but no result, any guess?
- Why am I not able to see the function call neither in logs nor in assembly code ? It is possible that they use a lower system library or something like that?
Any hint ?
Thanks !